Wi-Fi is everywhere—whether you’re streaming your favorite show, grinding through work emails, or just chilling on X with your phone. But here’s the deal: if your Wi-Fi security isn’t rock-solid, hackers can turn your network into their personal playground. That’s where MDK3 comes in, and I’m gonna break down how it helps you keep your Wi-Fi safe. It’s a badass tool that lets you test your Wi-Fi security by poking at weak spots in the IEEE 802.11 protocol. Think of it as a sparring partner for your wireless network, helping you spot vulnerabilities before the bad guys do.
Table of Contents
What’s the Deal with MDK3?
MDK3—short for Murder Death Kill 3, which sounds intense but is honestly just a name— is a tool built to test how secure your Wi-Fi network is. It’s like hiring an ethical hacker to stress-test your Wi-Fi setup. By mimicking attacks like deauthentication attacks or beacon flooding, it shows you where your network might crack under pressure. It’s a proof-of-concept tool, meaning it’s designed to say, “Hey, here’s what could go wrong if you don’t fix this.”
Whether you’re a network admin, a cybersecurity nerd, or just curious about keeping your Wi-Fi safe, MDK3 helps you find and patch holes in your wireless network. It’s not about causing chaos—it’s about making sure your Wi-Fi can stand up to real-world threats.
Why Should You Care About MDK3?
Here’s why MDK3 is worth your time if you’re serious about Wi-Fi security:
- Spot Weaknesses: It finds gaps in your wireless network before hackers can exploit them.
- Test Toughness: By throwing attacks like deauthentication attacks at your network, it shows how well it holds up.
- Keep Data Safe: A secure Wi-Fi network protects your personal stuff—like passwords or bank details—from being snatched.
- Learn Ethical Hacking: If you’re into penetration testing, MDK3 is a killer tool for practicing with permission.
Basically, MDK3 helps you sleep better knowing your Wi-Fi security is rock-solid.
Setting Up MDK3 on Kali Linux
Getting MDK3 up and running on Kali Linux is super easy. Kali’s the go-to operating system for security folks, so it’s perfect for this. Here’s how to do it, step by step.
Step 1: Update Your System
First things first, let’s make sure your Kali Linux is fresh and ready. Open your terminal and type:
sudo apt-get updateThis grabs the latest package lists, so you’re not installing some outdated version of MDK3.
Step 2: Install MDK3
Now, let’s get MDK3 on your system. Run this:
sudo apt-get install mdk3It’s quick, and in a minute or two, you’ll have MDK3 ready to roll.
Step 3: Double-Check It’s Installed
To make sure everything went smoothly, check the version of MDK3:
mdk3 --versionIf you see a version number pop up, you’re good to go. Wanna see what MDK3 can do? Type mdk3 --help for a list of commands.
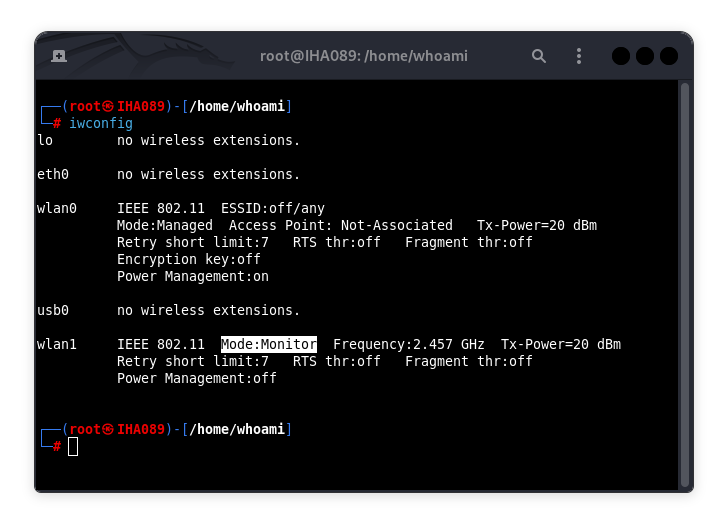
Step 4: Grab a Wi-Fi Adapter with Monitor Mode
Here’s the deal: MDK3 needs a Wi-Fi adapter that supports monitor mode. This lets your adapter eavesdrop on wireless traffic without joining a network—super useful for penetration testing or sniffing out network issues. Adapters like the Alfa AWUS036NHA are fan favorites for this, but check that your adapter supports monitor mode before you start. No monitor mode, no MDK3 magic.
What Can MDK3 Do? Exploring Its Test Modes
MDK3 is like a toolbox full of ways to test your Wi-Fi security. Each test mode mimics a different kind of attack, helping you see where your wireless network might be vulnerable. Let’s break down the main ones, with commands you can try (with permission, of course!).
Beacon Flood Mode
This one’s fun—it floods the air with fake Wi-Fi networks (called access points or APs) using beacon flooding. It confuses devices and can even crash some network scanners.
Random Fake Wi-Fi
mdk3 <interface> b Replace <interface> with your Wi-Fi adapter’s name (like wlan0). This creates a bunch of random fake APs, making nearby devices think there’s a Wi-Fi party going on.
Custom Fake Wi-Fi
Wanna name your fake Wi-Fi networks? Make a text file (say, fakenetworks.txt) and list names like: FreeWiFiHere CoffeeShopNet TotallyNotHacking Then run: mdk3 <interface> b -f fakenetworks.txt This broadcasts your custom Wi-Fi names, flooding the area with fake APs.
Authentication Denial-of-Service (DoS)
This mode hammers access points with authentication requests, potentially overwhelming them and kicking users off the wireless network.
mdk3 <interface> aIt’s like spamming an AP until it can’t handle legit users anymore—a classic denial-of-service attack.
Probing and ESSID Bruteforce
Curious about hidden Wi-Fi networks? This mode sends probe requests to find APs or guess unadvertised network names (ESSIDs).
mdk3 <interface> p -e <ESSID>It’s awesome for network reconnaissance, helping you map out what’s around or uncover sneaky hidden networks.
Deauthentication/Disassociation Mode
This is where deauthentication attacks come in. It sends packets to boot users off their Wi-Fi, causing major disruption.
mdk3 <interface> dThis floods the network with deauthentication packets, testing how easily clients can be disconnected.
Channel Jamming
Want to make a Wi-Fi channel unusable? This mode floods a specific channel with interference.
mdk3 <interface> d -c <channel>Swap <channel> for a number (like 6). It’s a harsh way to test a channel’s strength.
Michael Shutdown (TKIP)
This targets weaknesses in TKIP encryption, shutting down traffic on vulnerable wireless networks.
mdk3 <interface> m -t <MAC>Use the AP’s MAC address to mess with TKIP-based networks.
802.1X Testing
This mode floods the network with EAPOL packets to stress-test 802.1X authentication.
mdk3 <interface> xIt’s a DoS attack on the authentication process, showing how secure it really is.
WIDS/WIPS/WDS Confusion
This one messes with Wireless Intrusion Detection/Prevention Systems (WIDS/WIPS) by pretending multiple clients are connected.
mdk3 <interface> w -e <ESSID>It can trick security systems into freaking out, exposing their weaknesses.
MAC Filter Bruteforce
This tries to get past MAC address filtering by testing known client MAC addresses.
mdk3 <interface> f -t <MAC>It’s a smart way to check if your AP’s filtering is up to snuff.
WPA Downgrade Test
This tests if a network can be tricked into using weaker encryption, like WEP instead of WPA.
mdk3 <interface> gIt’s a key test for spotting encryption flaws in Wi-Fi security.
Whitelist and Blacklist Devices
- Blacklist Jamming:
mdk3 <interface> d -c <channel> -b <blacklist_file>This targets devices listed in your blacklist file, jamming them on a specific channel. - Whitelist Protection:
mdk3 <interface> d -c <channel> -w <whitelist_file>This keeps devices in your whitelist safe from jamming.
How to Protect Your Wi-Fi from Jamming
Jamming attacks can mess up your wireless network, but you’re not defenseless. Here’s how to keep your Wi-Fi secure:
- Lock It Down with Encryption
- Watch for Trouble
- Switch Channels
- Guard Your Gear
- Stay Updated
These steps make your wireless network a fortress against jamming and other attacks.
Using MDK3 Responsibly
MDK3 is a powerful tool, but it’s not for pranks or causing trouble. Using it without permission is illegal and can get you in serious hot water. Always get the network owner’s okay before running tests. When used ethically, MDK3 is a superhero for Wi-Fi security, helping you protect data and strengthen your wireless network. It’s about making things safer, not breaking them.
Final Thoughts
MDK3 is your secret weapon for mastering Wi-Fi security. From beacon flooding to deauthentication attacks, it lets you test your wireless network like a pro, finding weak spots before hackers do. But it’s not just about the tech—it’s about using it wisely to keep your Wi-Fi safe and your data secure. Whether you’re a network admin or just want to geek out on cybersecurity, MDK3 is a tool that empowers you to take control. So, set it up, test responsibly, and keep your Wi-Fi security on point!
Wi-Fi Jamming Techniques with MDK3: Advanced Strategies for Network Disruption