PDF files are a staple for document sharing and communication. But did you know that you can embed JavaScript code into a PDF? This opens up possibilities for automated actions, dynamic behaviors, and, in the realm of security research, testing vulnerabilities in systems and applications. In this blog post, we’ll introduce you to script2PDF, a Python tool designed for embedding JavaScript into PDF files. We’ll explore how to install, use, and understand its inner workings, as well as discuss how it can assist bug hunters.
Table of Contents
What is script2PDF?
script2PDF is a Python-based tool that allows users to embed JavaScript into PDF files. Whether you’re automating PDF functionalities or testing the security of PDF viewers and systems, this tool provides a straightforward way to inject JavaScript into a PDF’s action catalog. Designed for researchers, developers, and security professionals, script2PDF simplifies the process of embedding code into PDFs.
Installation of script2PDF
Getting started with script2PDF is easy. The tool is hosted on GitHub, and you can clone the repository to your local system. Follow these steps:
1. Open your terminal and run the following command to clone the repository:
git clone https://github.com/IHA089/script2PDF.git
2. Navigate to the script2PDF directory:
cd script2PDF3. Ensure you have Python installed on your system. script2PDF requires Python 3 and the PyPDF2 library. Install the necessary dependency:
pip install PyPDF24. You’re all set to use script2PDF!
Using script2PDF
The usage of script2PDF is straightforward and entirely command-line-based. Here’s how you can embed JavaScript into a PDF:
1. Run the script with the following command:
python3 script2PDF.py <path_to_pdf_file> <path_to_js_file>Replace <path_to_pdf_file> with the path to your PDF and <path_to_js_file> with the path to your JavaScript file.
Example:
1. Save the following JavaScript code in a file named script.js:
app.alert("An alert message from IHA089");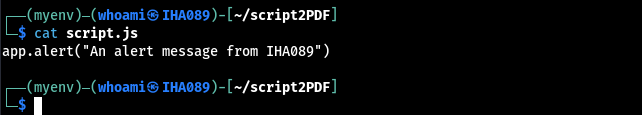
2. Assume you have a PDF file named sample.pdf in the same directory.
3. Run the script to embed the JavaScript payload:
python3 script2PDF.py sample.pdf script.js
4. After execution, you’ll have a new file named js_injected_sample.pdf. When opened in a compatible PDF viewer, you’ll see the following alert:
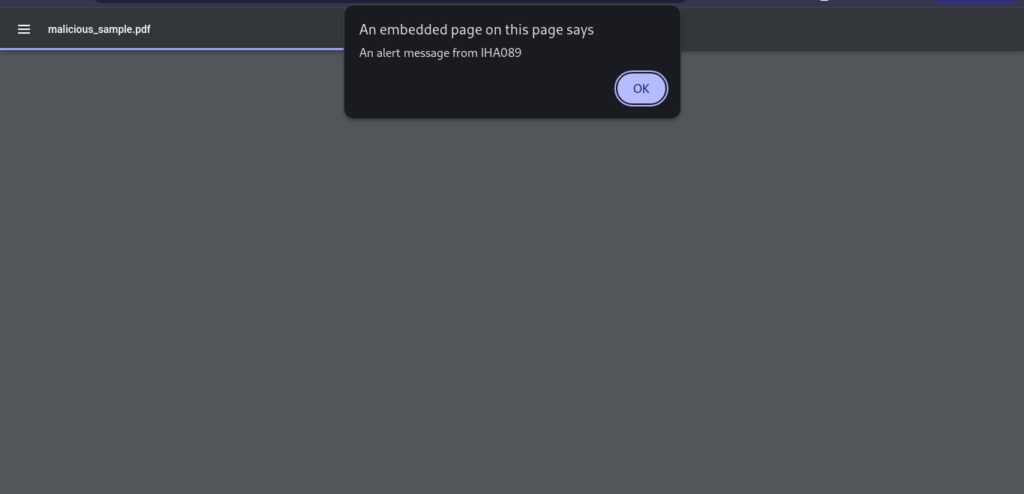
In the screenshot above, you can see the payload was executed successfully when the PDF was opened.
How script2PDF Works
The script2PDF tool leverages the PyPDF2 library to modify the PDF’s structure. Here’s a high-level overview of its workflow:
- Load the PDF: The tool uses
PyPDF2to open the PDF file and parse its structure. - Embed JavaScript: It creates a new JavaScript action object and embeds the JavaScript code from the provided file into the PDF’s action catalog.
- Save the File: The modified PDF is saved with a new name, ensuring the original file remains untouched.
This simple yet effective process ensures seamless injection of JavaScript code into any compatible PDF file.
How It Helps Bug Hunters
For ethical hackers and bug bounty hunters, It can be a powerful addition to your toolkit. Here’s how it can assist:
- Testing PDF Viewers:
- Identify outdated or vulnerable PDF viewers that fail to sandbox JavaScript effectively.
- Explore inconsistencies in how different viewers handle embedded JavaScript.
- Simulating Real-World Attacks:
- Embed payloads to test for Cross-Site Request Forgery (CSRF) or other vulnerabilities.
- Automate actions that trigger sensitive behaviors in systems.
- Crafting Proof-of-Concept Payloads:
- Demonstrate how embedded JavaScript can exploit weakly configured systems or endpoints.
- Test for security misconfigurations in file upload functionalities or document processing workflows.
- Learning and Experimentation:
- Understand the limits of JavaScript in PDFs.
- Experiment with different payloads to learn about PDF security.
Understanding the Technique
What Are the Limitations of JavaScript in PDFs?
While embedding JavaScript in PDFs has many possibilities, there are inherent limitations:
- PDF JavaScript Sandbox:
- Most modern PDF readers execute JavaScript in a sandboxed environment. This limits access to system resources or browser contexts, such as cookies or local storage.
- Cross-Origin Restrictions:
- JavaScript in PDFs lacks a valid web origin, preventing it from accessing browser-based resources.
- Security Measures in Viewers:
- Modern PDF readers (e.g., Adobe Acrobat, Foxit Reader) block unauthorized network requests, disable JavaScript by default, or prompt users before execution.
- Viewer Variability:
- Not all PDF viewers support JavaScript, and functionality may differ between platforms.
What Can You Do With This Technique?
Despite these restrictions, you can:
- Automate PDF interactions, such as filling forms or navigating pages.
- Trigger external actions, like opening URLs or making HTTP requests.
- Simulate attacks to identify weak protections, such as missing CSRF defenses.
Use It Responsibly: Embedding JavaScript in PDFs has legitimate uses for testing and research, but it can also be misused for malicious purposes. Always obtain proper authorization before testing systems, and adhere to ethical hacking principles and legal guidelines. Unauthorized use may lead to serious legal consequences.
It is a robust tool for embedding JavaScript into PDF files, making it invaluable for researchers and bug bounty hunters. By understanding the limitations and possibilities of JavaScript in PDFs, you can uncover vulnerabilities, craft proof-of-concept payloads, and push the boundaries of security research. Download the tool from GitHub and start experimenting responsibly with this fascinating technique.
Remember, the goal is always ethical hacking and responsible disclosure. Let script2PDF empower your research and innovation!


