Security testers and ethical hackers utilize their instruments to maximize the results in the field of web application hacking. One such important tool is the gau which means Gathering of URLs and which can be described as the means of finding out possible attack vectors. In this post, we’ll explain in further detail, what gau is, how you can install it, as well as guidelines on how most efficiently you can use gau when it comes to bug hunting and bug bounty.
Table of Contents
What is gau?
gau, short for GetAllURLs, is a powerful open-source tool developed by the team at lc. It aids bug finders and developers to obtain URL lists from web archives including way back machine, common crawl and more. As we have noted, these URLs may point to dormant straggler endpoints, old application releases or installation directories and others which are nominally contained but are potential security exposures.
Key Features of gau:
- Wide Data Source Integration: Gather links from more than one archive, so that no archive is missed out during the scanning process.
- Fast and Lightweight:
gauhas been written in Go language and therefore is very efficient and performs the computation very fast. - Simple Interface: Easy to use command-line options for the layman end-user.
- Highly Customizable: Refine information to targeted sets by such elements as parameters and flags.
Why Apply gau in Bug Hunting?
- Discover Hidden Endpoints: Identify other end points which are probably not configurable from the current over-arching web version.
- Identify Deprecated APIs: Older URLs may still be live to get a feeling about weaknesses stemming from stale code.
- Automate Reconnaissance: This will help save time as a result of automation of the process of linking from the archived URLs.
How to Install gau
The installation of gau is relatively simple, if one has the pre requisites. Follow these step-by-step instructions to get started:
Step 1: Install Go
It is written in Go language, so there are a few things you have to do to get it installed.
On Linux:
sudo apt update;
sudo apt install golang-go -yOn macOS:
brew install goAfter installation, verify it with:
go versionStep 2: Install gau from source
Use the following command to install gau:
go install github.com/lc/gau/v2/cmd/gau@latestUse the command below to make it run from any terminal location
sudo mv ~/go/gau /usr/local/binStep 3: Setup .toml file
curl https://raw.githubusercontent.com/lc/gau/refs/heads/master/.gau.toml > ~/.gau.tomlStep 4: Verify the Installation
Once installed, check if gau is working by running:
gau --versionThis command should give details of version of gau.
Basic Commands and Usage
gau ,however is now established, therefore it’s now about how to get the best out of it.
Fetch URLs for a Target Domain
The simplest command fetches all available URLs for a domain:
gau example.comor
echo "example.com" | gau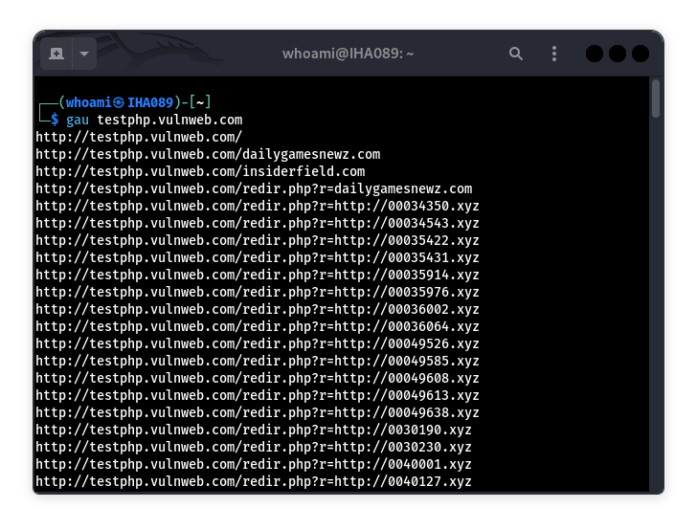
Fetch Only Subdomains
gau can also help you focus on subdomains:
gau --subs example.com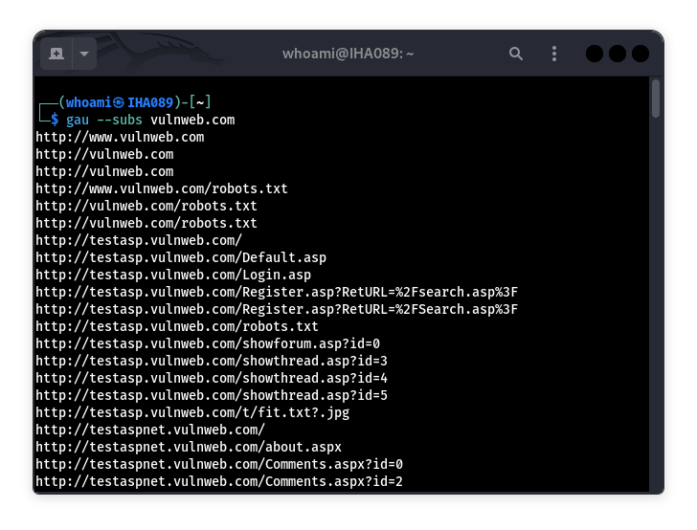
Combine gau with Other Tools
Combine gau with other tools like gf (Gf-Patterns) for advanced filtering:
gau example.com | gf xss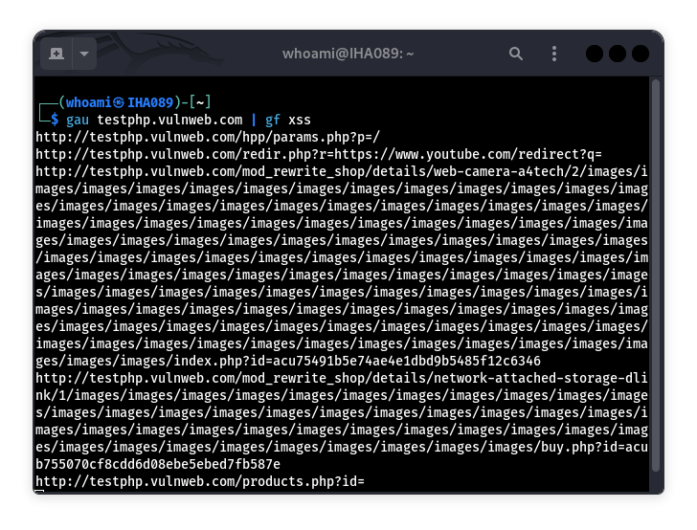
Advanced Techniques
Using gau in Automated Recon
You can integrate gau into your recon scripts for automation:
#!/bin/bash
domain=$1
mkdir -p recon/$domain
gau $domain | tee recon/$domain/urls.txtCombining gau with Wayback URLs
For an even larger set of results, combine gau with waybackurls:
gau example.com | waybackurls > combined_urls.txtIdentify Parameters for Vulnerability Testing
gau helps identify parameterized URLs, which are great targets for injection attacks:
gau example.com | grep '?'Why we use gau?
Locate Deprecated Pages
Web archives typically provide URLs of pages that have been removed from other active uses. These may reveal information or improper configurations connected with the product.
Population of Client-Side Vulnerabilities
For collection of .js files use gau and them thoroughly for critical information or security vulnerabilities.
Data points and insights: Misconfigured Endpoints
URLs saved in an archive can go to test environments or an incorrectly configured admin panel.
How gau can be Utilized to the Fullest
- Use Proxies for Large Targets: For large domains, pass route requests through a proxy if you do not want to be rate-limited.
- Combine with Other Recon Tools: When used together with gooscan, jmptr, map, and portvista, leverage
gauin combination with wordlistsamass,subfinder, andhttpxfor further recon. - Validate URLs: Sometimes we collect URLs and which are not active anymore, so make sure and validate it using tools like
httprobe.
Mistakes Made and Solutions to Them
- Fetching Fewer URLs: Examine the sources for which
gauis designed to provide frequency. Some of the archives may contain less data in the particular domains of the objects. - Compatibility Issues: Go Version Go on to check whether you are using the latest Go version. Newer releases of Go could be needed by
gau.
gau is of huge importance in the world of bug hunting ethical hackers. It can obtain files that were stored at specific URLs in the past, which in turn gives the tool truly powerful insight into the applications retrieved based on URLs, opening up previously unseen exploitable vulnerabilities.
No matter if you’re a beginner in bug hunting or seek to improve your experience, gau will definitely be helpful. Therefore, Install it, and check out all the nooks and crannies of your target applications!
If you found this guide helpful, share it with fellow hackers and let us know your favorite use cases for gau in the comments!


