What it is, why it matters, and how the exploitation works
A critical security vulnerability has been identified in n8n, the popular open-source workflow automation platform. Tracked as CVE-2025-68613, this flaw allows an authenticated user with workflow edit permissions to run arbitrary JavaScript code on the server hosting n8n — potentially leading to total system compromise. (NVD)
n8n is widely used by developers, DevOps teams, and enterprises to automate tasks, connect services, and orchestrate workflows. Because it is often connected to internal APIs, databases, cloud credentials, and sensitive systems, a flaw like this poses a significant threat to security teams everywhere. (SecureLayer7 Blog)
Why This Vulnerability Is Critical
CVE-2025-68613 stems from the way n8n evaluates expressions embedded inside workflows. In n8n, users can insert expressions — typically wrapped in {{ }} — that the platform interprets as JavaScript at runtime. Ideally, this evaluation happens in a restricted context that prevents access to sensitive APIs or system resources.
In affected versions of n8n, however, this sandboxing is insufficient. Under the right conditions, an attacker can escalate from benign expressions to malicious code that runs with the same privileges as the n8n process itself. (Feedly)
This isn’t just a theoretical risk: successful exploitation means:
- Arbitrary system commands can be executed.
- Sensitive files can be read or modified.
- Environment variables containing API keys or passwords may be exfiltrated.
- Persistent backdoors or reverse shells can be established. (TheHackerWire)
High-Level Exploitation Overview
Unlike simple logic bypasses, CVE-2025-68613 abuses the core expression evaluation mechanism inside n8n.
A workflow editor or automation designer — even one with relatively low privileges — can create or edit a workflow and supply an expression that n8n will evaluate.
The key insight is this: n8n executes expressions using Node.js, and if the sandbox is not properly isolated, the expression can interact with powerful Node.js modules like child_process to run system commands.
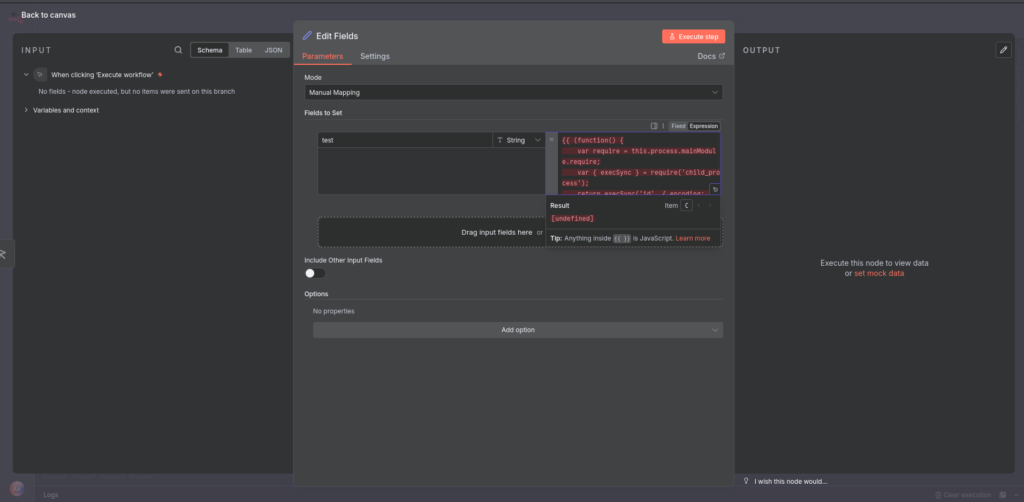
A minimal example of such a payload (used by exploit researchers to demonstrate RCE) looks like this:
{{ (function() {
var require = this.process.mainModule.require;
var { execSync } = require('child_process');
return execSync('id', { encoding: 'utf8' }).trim();
})() }}
This code is wrapped in the standard expression format n8n expects ({{ }}), but because the execution context allows access to require, it can load the child_process module and call execSync() to run arbitrary OS commands.
The id command is often used to validate exploitation because its output reveals the user identity under which the code is running — often the system account executing n8n. If that process runs as a privileged user, the attacker effectively gains those privileges.
Step-by-Step: How the Exploit Works
Here’s an abstracted view of the exploitation flow to help you understand without copying other guides:
1. Authenticate & Gain Expression Access
The attacker first authenticates to the n8n instance — this could be a legitimate account or one created through open registration. What matters is that the account has workflow edit permissions.
2. Inject Malicious Expression
Inside the workflow editor — typically in nodes like Set, Function, or any expression-enabled field — the attacker inserts a crafted expression similar to the one above. Because n8n evaluates this expression server-side, placing the payload here is the key exploitation step.
3. Trigger Workflow Execution
Once the expression is in place, the attacker executes the workflow. n8n evaluates the expression as part of workflow processing, and because the sandbox is not effective, the payload gets executed by the Node.js runtime directly.
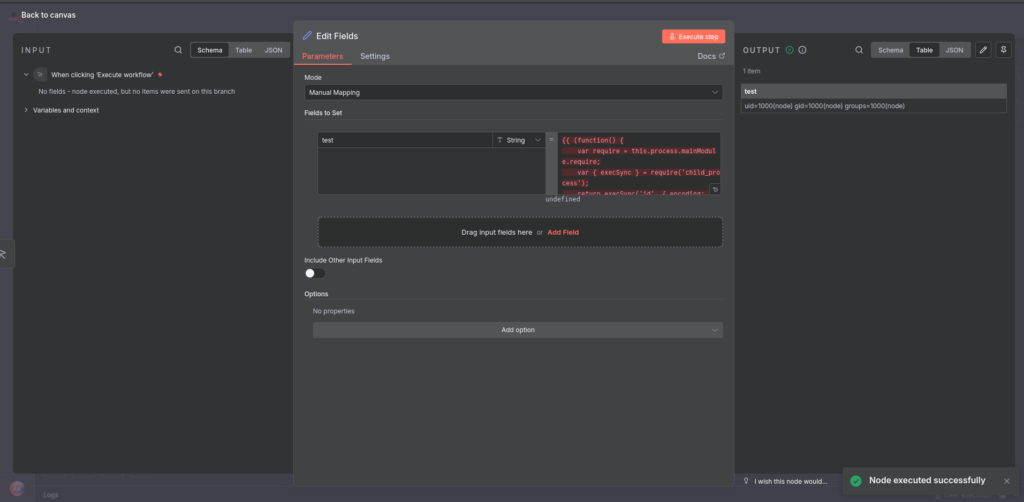
4. Observe or Act on Output
The output of the exploit can be observed in the workflow’s results. For example, the id command returns the user under which the process is running. Other commands can read sensitive files, expose credentials, or establish outbound connections.
Real-World Impact Scenarios
The true danger of this vulnerability lies in what attackers can do after initial exploitation:
- Credential Theft: By reading environment variables or configuration files, attackers can harvest cloud credentials or database passwords.
- Lateral Movement: With system command execution, attackers can traverse the host machine and connected networks.
- Persistence: Creating scheduled tasks, cron jobs, or reverse shells enables long-term access.
- Service Disruption: Critical automation workflows can be modified or destroyed, impacting business continuity.
Given n8n’s integration with internal systems and data sources, these risks extend well beyond the application itself.
Mitigation and Defensive Measures
The primary mitigation is to update n8n to a patched version. According to public vulnerability data, patches for this issue are included in versions 1.120.4, 1.121.1, and 1.122.0 or later. (Incibe)
Other defensive steps include:
- Restrict workflow editing permissions only to trusted administrators.
- Harden the execution environment by running n8n with minimal privileges (e.g., dedicated service account).
- Audit existing workflows for dangerous expressions that reference internal Node.js objects like
processor modules likechild_process. - Monitor logs for unusual command outputs or unexpected external connections.
Conclusion
CVE-2025-68613 is a high-impact vulnerability in n8n’s expression evaluation system that allows authenticated users to execute arbitrary code on the host server. Its critical severity and real-world exploitability make it a must-address risk for any organization using n8n in production.
By understanding both the root cause of the flaw and the mechanics of exploitation — including how expressions can be abused to escalate into full RCE — defenders can better protect their environments and respond effectively.
Secret Subdomain Finder: Advanced Recon Tricks for Your Next Bug Bounty


