Hey there, fellow bug hunters! If you’re an ethical hacker looking to up your game, you know the right tools can make all the difference. I’ve spent years tracking down vulnerabilities, and I’m excited to share my top 10 go-to tools that help me uncover security flaws before the bad guys do. Whether you’re just starting out or a seasoned pro, these tools will help you find weaknesses, secure systems, and maybe even score some bug bounty rewards. Let’s dive in!
Table of Contents
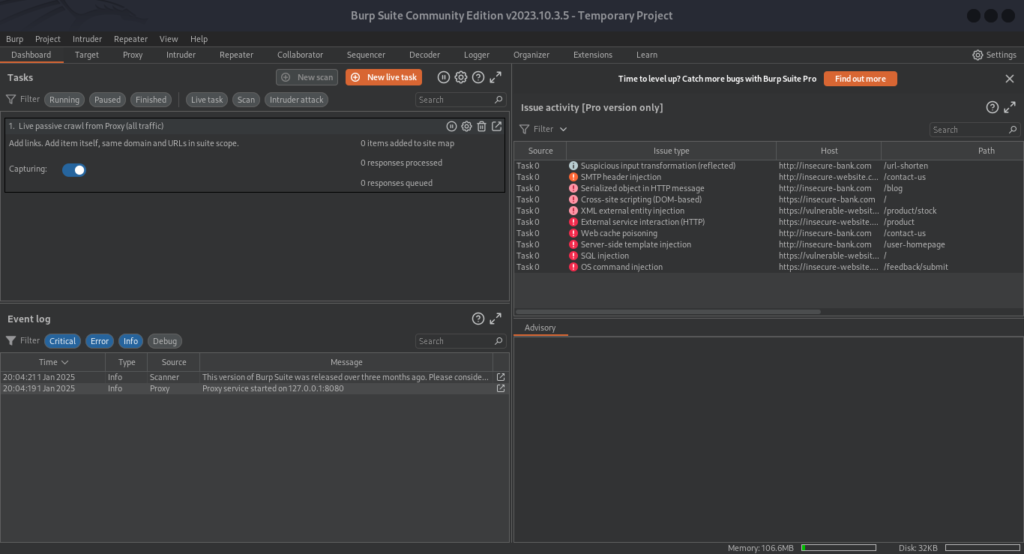
1. Burp Suite
Burp Suite is hands-down the best tool for web app security testing. It’s like having a superpower—I use it to intercept HTTP requests, automate scans, and dig deep with manual testing. Just last week, I caught a sneaky cross-site scripting (XSS) flaw on a login page by tweaking inputs with Burp’s Proxy. Its Scanner also flagged an outdated library I would’ve missed. You can even add extensions like Turbo Intruder for advanced fuzzing. It’s a game-changer for finding and exploiting web vulnerabilities.
The free Community Edition is great for beginners, but the Professional version’s automation features are worth the investment.
2. Nuclei
Nuclei is your best friend for fast, automated vulnerability scanning. It uses templates to spot misconfigurations, CVEs, and other flaws in record time. I recently scanned a web app with Nuclei and found a misconfigured CORS policy in minutes—saved me hours of manual work! You can also create custom templates to target specific issues, which is perfect for bug bounty hunters looking to scale their scans.
Check out the Nuclei template community on GitHub for the latest templates to catch new vulnerabilities.
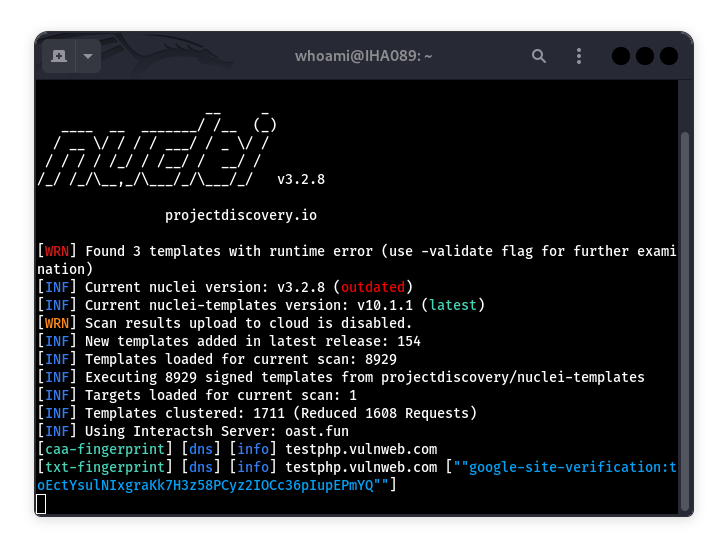
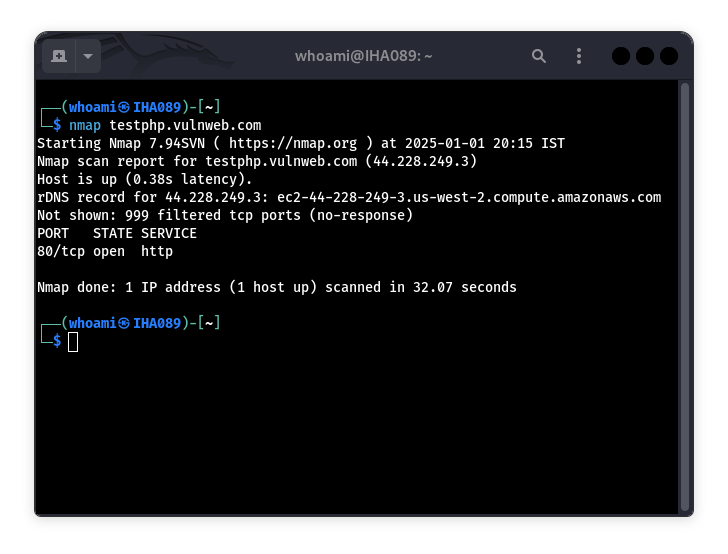
3. Nmap
Nmap is the king of network reconnaissance. I use it to map out open ports, services, and software versions on every project. A while back, I found an outdated FTP service on a client’s server using Nmap—it was vulnerable to a known exploit. The scripting engine (NSE) lets you run custom scripts for deeper checks, making it a must-have for understanding a network’s attack surface.
Quick Tip: Try the -sV flag to detect service versions, and add --script vuln for quick vulnerability scans.
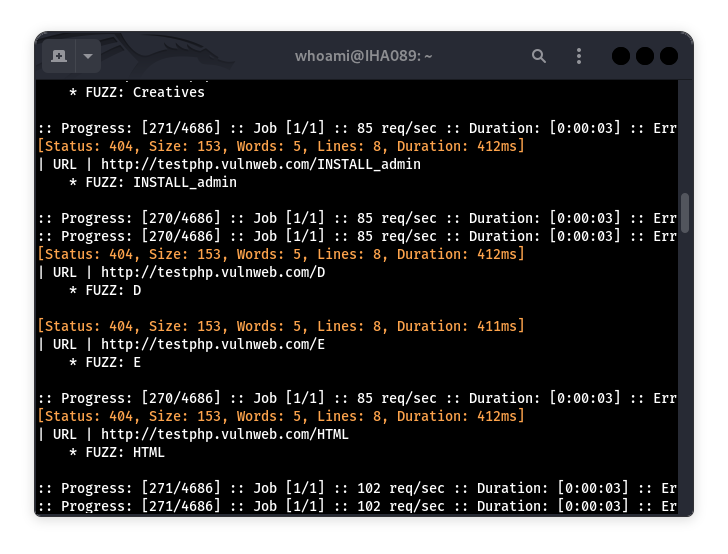
4. FFUF
FFUF (Fuzz Faster U Fool) is a web fuzzing beast. It’s super fast and helps you uncover hidden directories, files, and parameters. I once found a backup file (backup.zip) on a web server using FFUF—it had sensitive config data the client didn’t know was exposed. FFUF’s wordlist-based fuzzing is perfect for spotting misconfigured endpoints or forgotten files that could lead to a breach.
Pair FFUF with a solid wordlist like SecLists, and use -mc 200 to filter for successful responses.
5. Waybackurls
Waybackurls is a hidden gem for digging into a website’s past. It pulls URLs from the Wayback Machine (archive.org), revealing old pages that might still be vulnerable. I once found an outdated login page with a weak password reset feature using this tool—it was a goldmine for the client to fix. It’s a favorite for bug bounty hunters looking to uncover forgotten endpoints.
Pipe Waybackurls output into FFUF to fuzz the discovered URLs for live vulnerabilities.
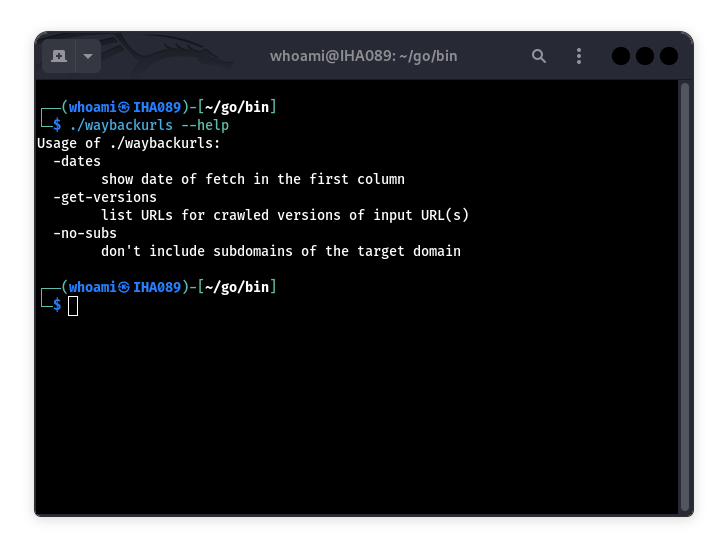
6. Amass
Amass is my go-to for subdomain enumeration. It pulls data from DNS servers, certificate logs, and more to map out a target’s attack surface. I recently found a forgotten subdomain (dev.example.com) running an old WordPress version with known vulnerabilities, all thanks to Amass. It’s perfect for gathering intel before launching targeted attacks.
Use the -active flag for deeper scans, but be careful—it can get noisy and might alert the target.
7. Wafw00f
Wafw00f helps you spot Web Application Firewalls (WAFs) on a target site. It sends HTTP requests and analyzes responses to identify WAF signatures. I used it to confirm a site was using Cloudflare’s WAF, which helped me tweak my payloads to bypass it. Knowing what WAF you’re up against is key to planning your next move.
If Wafw00f detects a WAF, look up its bypass techniques—some WAFs have well-known weaknesses.
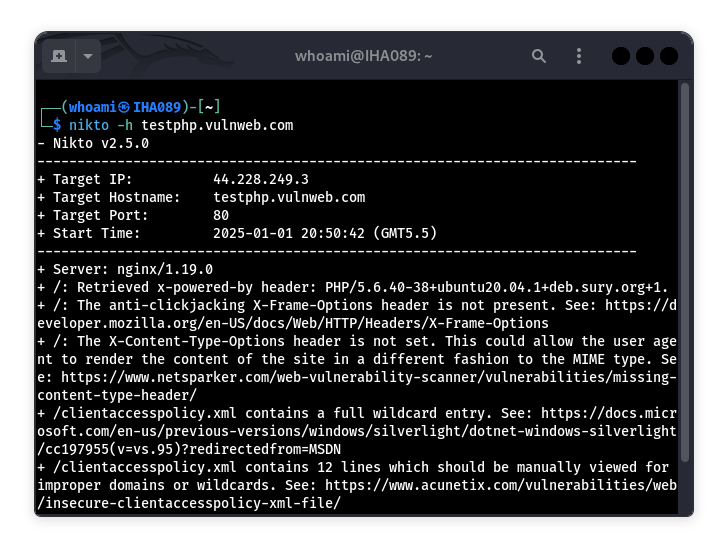
8. Nikto
Nikto is a reliable tool for quick web server scans. It checks for outdated software, dangerous files, and misconfigurations. I once found an exposed .git directory with Nikto that could’ve led to a source code leak. It also flags things like insecure headers or weak SSL configs. It’s not fancy, but it gets the job done for a first-pass scan.
Use the -Tuning option to focus on specific vulnerability types and speed up your scans.
9. Metasploit Framework
Metasploit Framework is a powerhouse for penetration testing. It’s loaded with exploits, payloads, and modules to simulate real-world attacks. I used it to exploit a known vulnerability in an outdated Apache server, showing the client exactly how an attacker could get in. From scanning to post-exploitation, Metasploit has it all, and its community keeps it fresh with new exploits.
Launch msfconsole and use the search command to find exploits tailored to your target.
10. Shodan
Shodan is like a hacker’s search engine—it scans internet-connected devices and exposes their weaknesses. I used it to find a client’s exposed IoT camera with default credentials, which was a huge security risk. Shodan is great for spotting misconfigured servers, routers, or IoT devices that might be part of your target’s network.
Use filters like port:80 os:Linux to narrow down your searches and find specific devices.
Level Up Your Bug Hunting
These 10 tools are your ticket to becoming a better bug hunter. I’ve seen them uncover game-changing vulnerabilities—like that exposed backup file with FFUF or the outdated server with Nmap. They cover every stage, from recon to exploitation, and they’ll help you secure systems while sharpening your skills. So, which tool are you trying first? Drop a comment below—I’d love to hear your thoughts!


