Real hackers don’t just test endpoints—they dissect every header.
Every time a browser loads a website, there’s an invisible negotiation—a quiet exchange of rules, permissions, and expectations written in HTTP headers. To most users, these are meaningless strings. To a hacker, they’re a roadmap.
Security headers and configuration settings are not flashy. They don’t scream vulnerability like a forgotten admin panel or an open S3 bucket. But when misconfigured—or worse, missing—they quietly dismantle your defense stack. For bug hunters and ethical hackers, this is where silent bounty gold lives.
Table of Contents
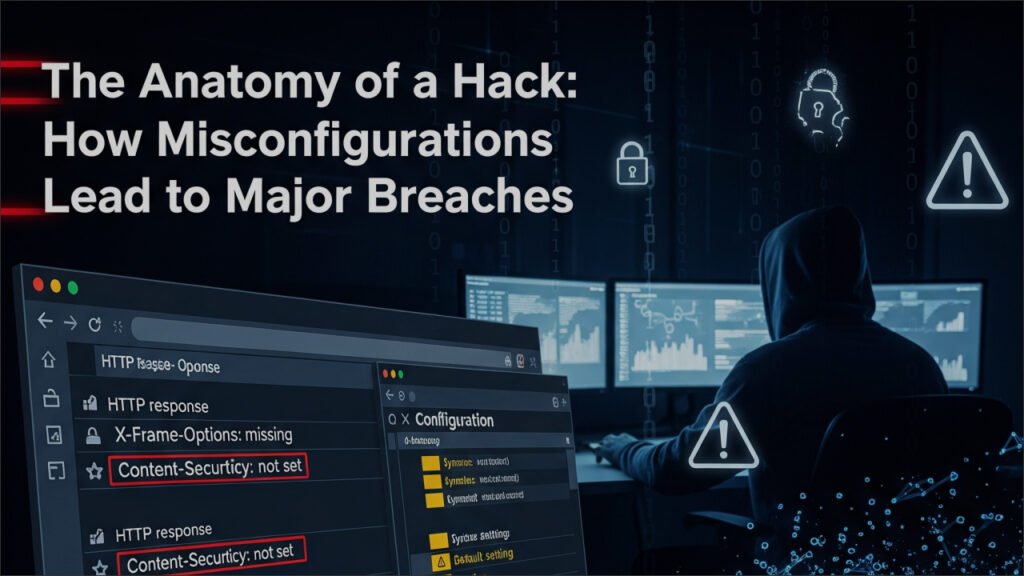
1. HTTP Header Analysis
Start with the basics, but interpret like a hacker:
- Server & X-Powered-By: Leaking tech stack? Tailor your exploits accordingly. If you see Apache/2.4.49, your brain should immediately recall the path traversal RCE in that version.
- X-Frame-Options: Absent? Think clickjacking. Is it set to ALLOWALL? Even better (for you).
- X-XSS-Protection: If it’s turned off, older browsers are exposed. It’s not your main vector, but it’s something to note.
- X-Content-Type-Options: Without nosniff, MIME confusion becomes a vector. Think file upload exploits.
It’s like decoding a secret note, wondering, “What’s this server spilling?” A scan shows an “X-Powered-By: PHP/5.6.40,” hinting at an outdated setup vulnerable to old bugs. The next step? Link this with TLS/SSL analysis to see if weak encryption amplifies the risk.
You’re not reading headers. You’re reading the developer’s mindset.
2. Cookie Flags Checking
Authentication often hinges on cookies. Your job? See how easily they can be stolen or manipulated.
- HttpOnly: Missing this? A basic XSS becomes a session hijack.
- Secure: Non-HTTPS cookies without Secure are fair game in a MITM scenario.
- SameSite: Without Strict or Lax, CSRF attacks get easier.
It’s a guard checking a vault, asking, “Can someone snatch this cookie?” A check finds a session cookie missing the “Secure” flag, ripe for HTTP snagging. Chain this with CORS policy checkers to see if cross-origin requests can grab it, turning a cookie flaw into a session hijack risk.
3. TLS/SSL Analysis
Every encrypted connection can tell you a story:
- Check for deprecated protocols (TLS 1.0/1.1)
- Weak ciphers = potential for downgrade attacks
- Self-signed or expired certs = trust issues
It’s a locksmith testing a padlock, wondering, “Can this be picked?” A scan flags TLS 1.0 with weak ciphers like DES, open to brute-force attacks. Link this with HTTP header analysis to check if exposed tech versions worsen the leak.
Go further—look for certificate pinning bypass possibilities on client-side apps. Explore if old TLS versions are accepted on alternate ports (like 8443).
4. CORS Policy Review
CORS isn’t just a developer annoyance. It’s a door. When open too wide, it becomes a weapon.
- Access-Control-Allow-Origin: * with Access-Control-Allow-Credentials: true? That’s a direct vulnerability.
- Reflected origins or dynamic origin echoing? That’s a red flag.
It’s a border patrol agent, asking, “Who’s sneaking across this line?” A check finds a wildcard Access-Control-Allow-Origin: *, letting any site pull data. Chain this with cookie flags checkers to show how attackers could steal sessions, turning a policy gap into a critical exploit.
Always test CORS misconfigurations in APIs and admin interfaces. That’s where sensitive data usually flows.
5. Content Security Policy (CSP)
CSP is meant to prevent XSS, but too often it’s either missing or misused:
- Are unsafe directives (unsafe-inline, unsafe-eval) used?
- Is everything whitelisted with *?
- Are script sources trusted via http:// instead of https://?
It’s a bouncer at a club, wondering, “Is this script on the guest list?” A validation finds no CSP or a weak one allowing unsafe-inline, leaving XSS doors open. Link this with HTTP header analysis to spot tech leaks that aid attacks.
CSP bypass via JSONP, outdated libraries, or vulnerable 3rd-party scripts. Don’t stop at validation—exploit the misconfig.
Real-World Chains: When Headers Crack the Whole System
One misconfigured header doesn’t mean much alone. But together?
- No X-Frame-Options + No SameSite = Clickjacking + CSRF = Silent Account Takeover
- Weak CSP + Reflected XSS + Missing HttpOnly = Token theft
- Improper CORS + Open redirect = Token exfiltration
This is where the hacker mindset wins—by seeing how to chain small weaknesses into critical bugs.
Conclusion: It’s Not Just What’s Missing. It’s Why It’s Missing.
Security headers and configurations are like a site’s immune system. When they’re missing or improperly configured, it tells you how much the devs care—or don’t. As a bug hunter, your job is to read between the lines of every response header and config and find what others overlook.
The next time someone tells you headers don’t matter, remind them: The best bugs hide in plain sight.